NAT Issues
Ideally difuse should be set up as an edge device, meaning it is directly connected to the internet with PPPoE or DHCP or whatever your ISP offers, but in some situations this is not possible and we end up in scenarios where there is another gateway and Difuse ends up being behind it. This can introduce significant hurdles in getting calls to work reliably but there are some ways you can get around most of the scenarios.
Common Steps
Universally there are some things that you need to do to make the PBX work behind NAT, we will go over some of them:
- Port Forwarding: If you're behind NAT it is crucial to have ports forwarded from the upstream gateway, for making things work with difuse there are a few ports that need to be forwarded depending on your use case:
- 6069: TLS: This is the SIP signaling port that we recommend you use
- 443: HTTPS: This is the port used by difuse for hosting it's own web server, this is also responsible for helping you provision phones like Cloud Softphone, Difuse Phone and Linphone
- 20000-30000: This port range is for RTP communication and is crucial for getting voice packets through.
Here's an example of port forwarding done no a Fortigate firewall:
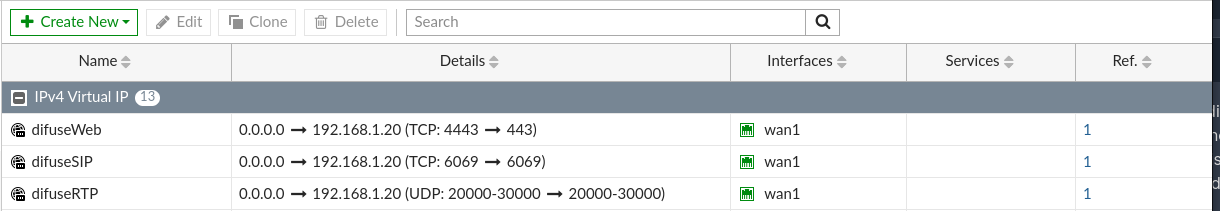
Fortigate - Port Forwarding
- Firewall: If you're behind a firewall like Fortigate or Sonicwall, we recommend you do the firewall setup there and on difuse just let the pseudo WAN range access LAN and other zones on the Difuse side.
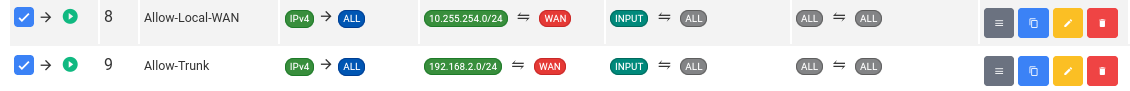
Difuse Firewall - Allow (Local) WAN
You might notice the Allow-Trunk rule there as well, this is to let the trunk range (which is part of a Custom Interface) also access the device via an INPUT rule.
- PBX NAT Options: On Difuse you need to let the PBX know that it is indeed behind a NAT this is done pretty easily by navigating to PBX -> Settings
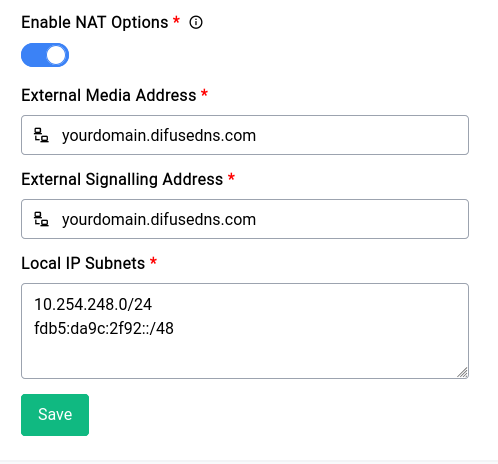
Make sure that the External Media Address and External Signalling Address are set to a domain that resolves to your actual public IP.
Local IP Subnets here means what subnets are local to the PBX, so for instance if you have a Fortigate firewall (lets assume range 10.254.248.0/24), and you're connected behind it, and there are clients let's assume desk phones who are also connecting to you from that range, you need to let the PBX know that it is infact "local" to you and does not need to traverse the internet (or set public IP in the SIP headers) to reach those peers reliably.

