Fortigate Firewall - NAT Setup
When Difuse is behind a Fortigate firewall there are some interesting things that need to be done to make things work smoothly.
Let's go over the steps in brief then in detail:
- Disable SIP ALG
- Make sure Difuse has outbound access
- Create Inbound rules to Difuse
Disabling SIP ALG
SIP ALG stands for Application Layer Gateway and is common in all many commercial routers. Its purpose is to prevent some of the problems caused by router firewalls by inspecting VoIP traffic (packets) and if necessary modifying it.
Even though it is meant to make things better it ends up making things worse so it's better to disable it entirely, it also causes some nasty vulnerabilities in your network so it is better to turn it off regardless. You can turn it off on fortigate devices using their CLI on the dashboard:
Next we're going to have to remove the session helper, this command will let you see the current session helpers:
Something similar to this will be displayed:
Since ours is at 13 we can run the following to delete it:
After this we recommend to restart the Firewall.
Making sure Difuse has outbound access
If your firewall allows you to access the internet without much hassle (meaning you're able to connect to WiFi and browse websites) then you can skip this step entirely, else you would need to add rules that will allow traffic from Difuse to go outside, it's good to allow all outbound traffic from difuse.
Creating Inbound Rules to Difuse
Create Virtual IP
You need to create 1 virtual IP per service port to forward to the Difuse PBX
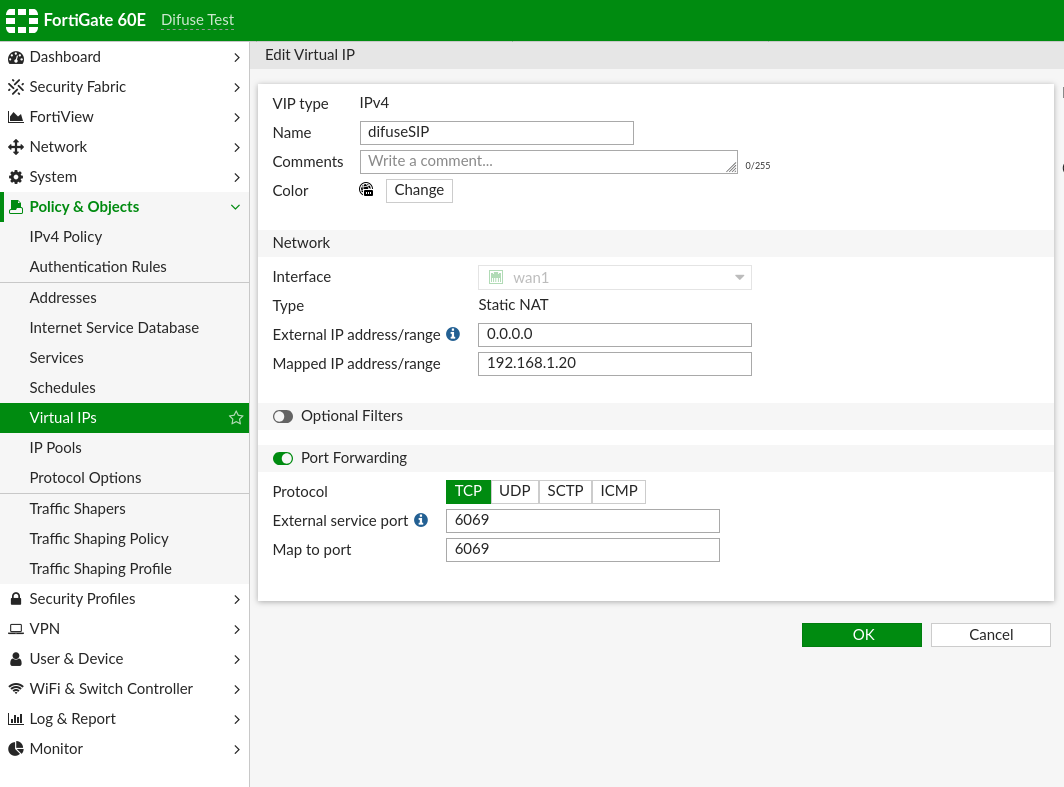
Fortigate - Virtual IP Example
The above is what it looks like for just the TLS SIP Port, it should be done for all the services that you want to forward from Fortigate to Difuse. In the end your Virtual IPs list will look like this:

Fortigate - Virtual IPs List
Now moving on to IPv4 Policy you need to setup rules there as well so that connections are allowed it'll look something like this when done:
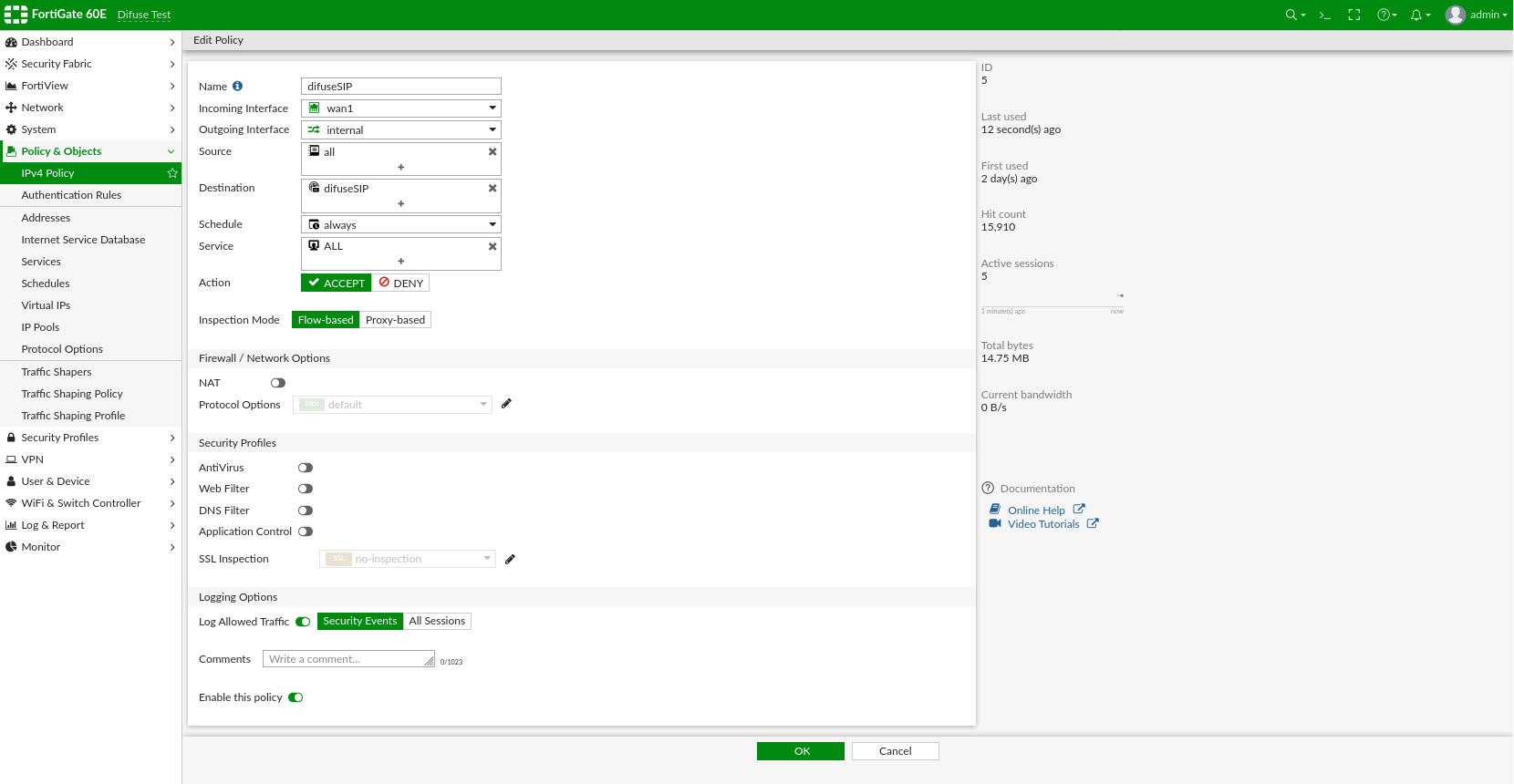
Fortigate - SIP IPv4 Policy

Fortigate - IPv4 Policy
All that being done along with setting the NAT options properly in Difuse as per the common guide, you should be good to go.

