This is not the latest version of this documentation, for the one that is upto date, please see the latest version (2.7.0)
Traffic Rules
Traffic rules are used to control the flow of incoming and outgoing traffic on a network. These rules specify the conditions under which traffic is allowed or denied, as well as the actions that should be taken when these conditions are met.
For purposes of demonstration we are going to create 4 firewall rules:
- A rule that allows connections to all the SIP and RTP ports which are:
- SIP: 6067 (UDP)
- SIP: 6068 (TCP)
- SIP TLS: 6069 (TCP)
- RTP: 20000-30000 (UDP)
- A rule that allows for remote administration of Difuse using the TCP ports 80 and 443.
- A rule that let’s all traffic through to a specific globally routable IPv6 address.
Allowing SIP and RTP connections
This is what adding the rule should look like:
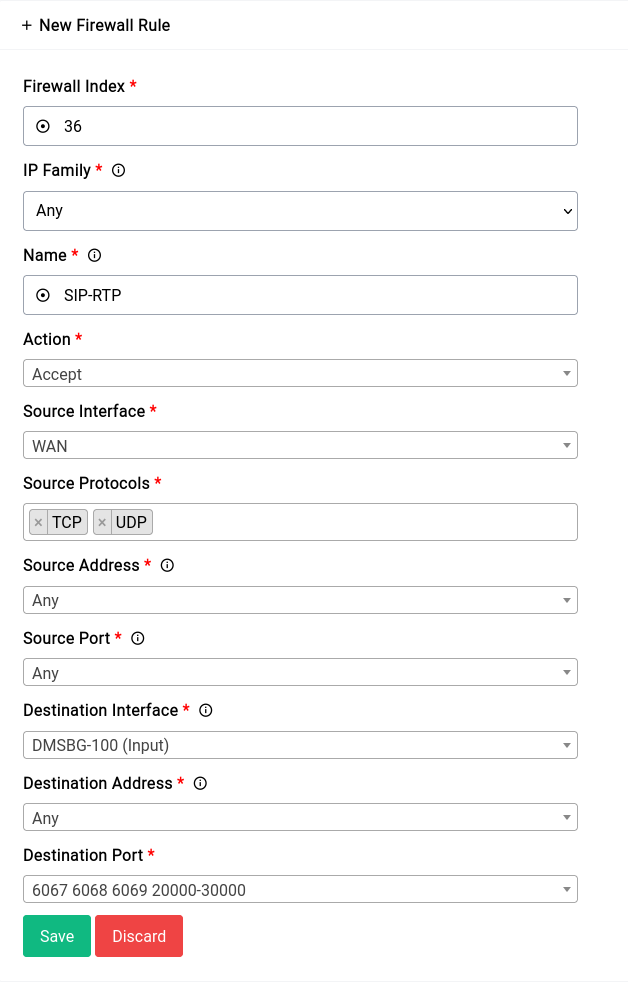
Firewall - Traffic Rules - Adding A Rule
Now once you add a rule, it doesn’t get applied right away. You can see that there’s a red pill that pops up near the title
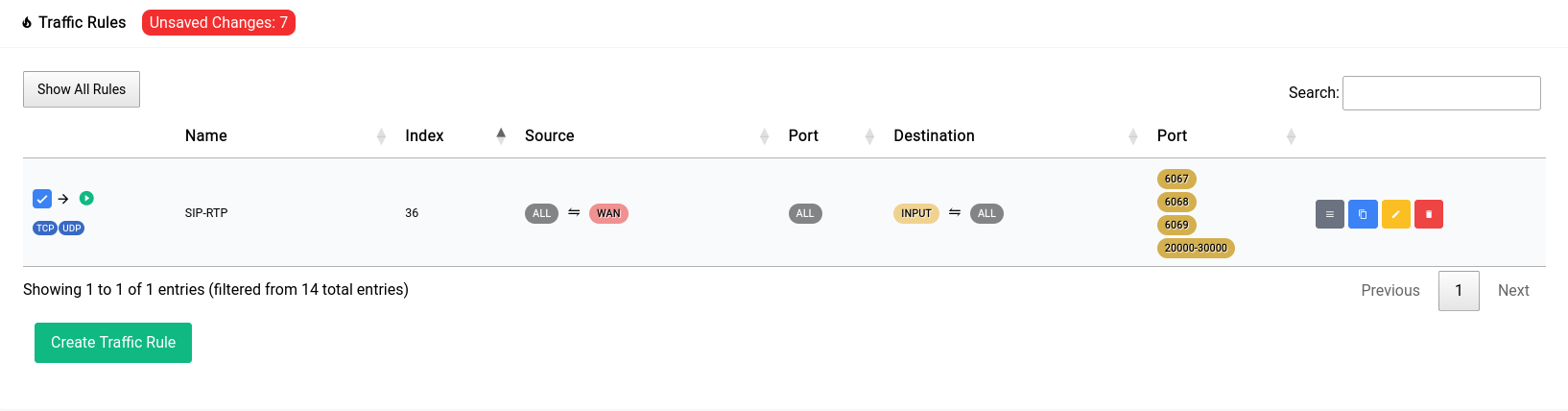
Firewall - Traffic Rules - Tabulation
When you click on it, it shows you a gist of the things that have been changed:
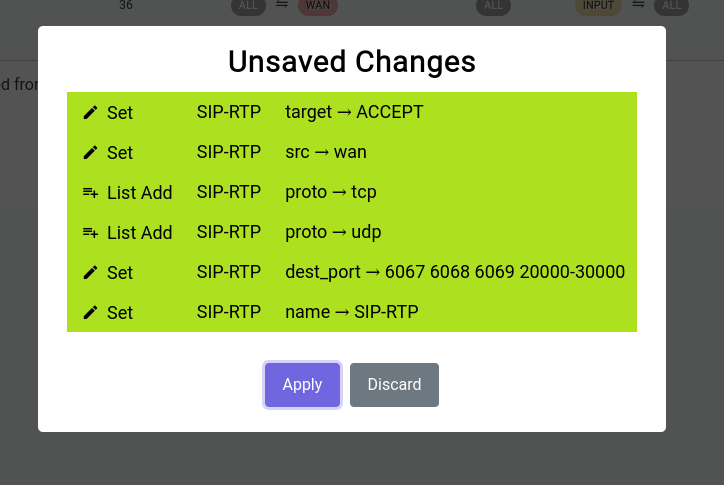
Firewall - Traffic Rules - Unsaved Changes
It’s really not a good idea to keep these unsaved changes for a long time as they’re ephemeral and have to be committed to disk or discarded at some point in time.
Once you click apply you will see it go away and the rule you added will show up in the table as such:
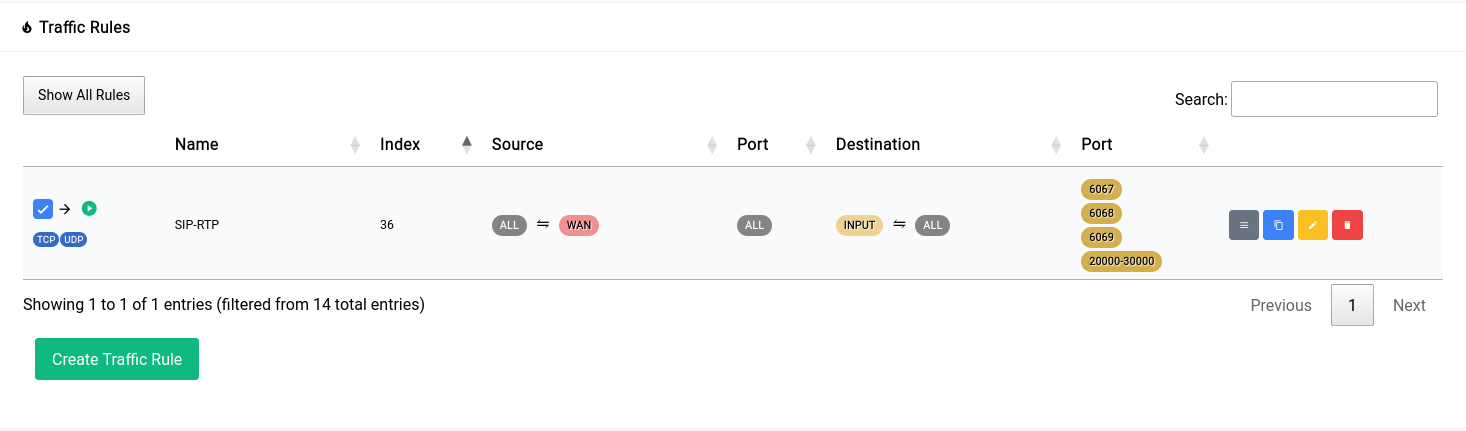
Firewall - Traffic Rules - Saved Table
Allowing Remote Administration
For this rule we’re gonna make use of a Ports Alias. Namely the “HTTP” alias that has the ports 80 and 443 defined. This is just for demonstration you could also just specify the ports directly with a space in between them.
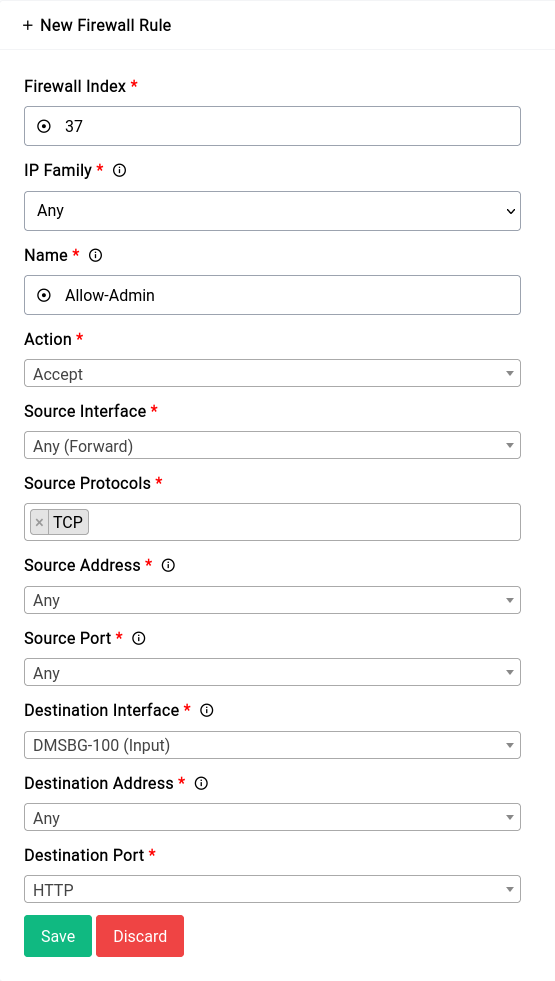
Firewall - Traffic Rules - Alias Based Rule
The unsaved changes modal should look something like this:
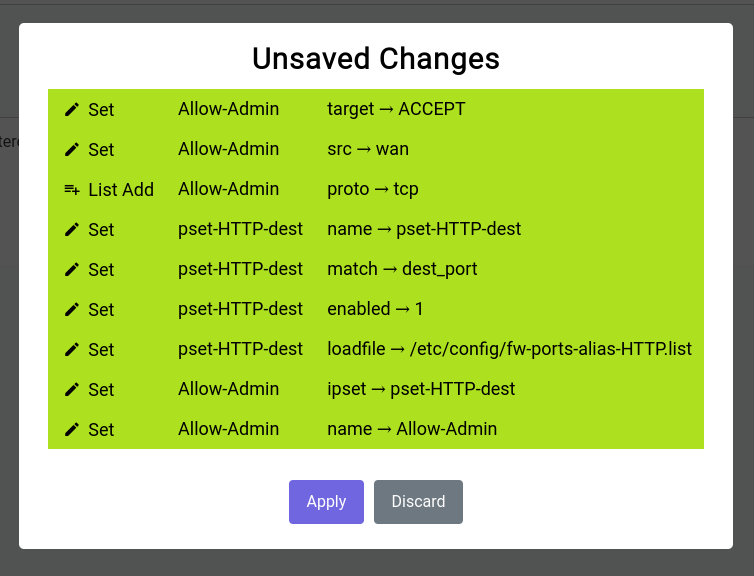
Firewall - Traffic Rules - Unsaved Changes
After the rule has been made the table should look something like this:
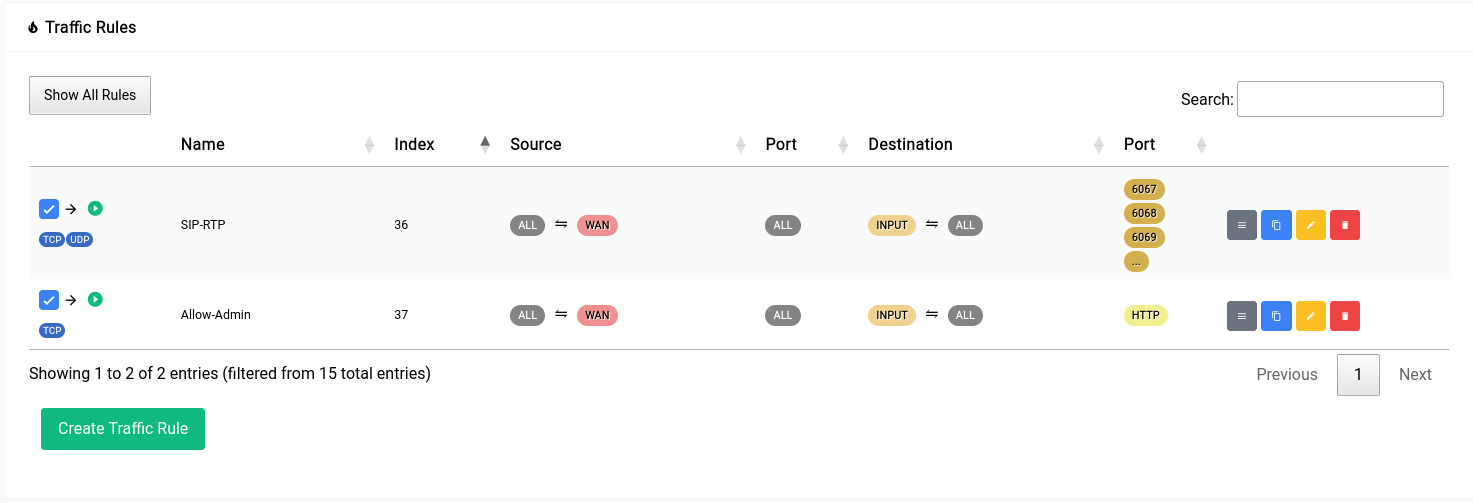
Firewall - Traffic rules - New Rule in Table
Allowing All Traffic to a Specific IPv6 Address
If your ISP hands out a sufficiently large prefix (/64 or below) all devices on the host network should already have a globally routable IPv6 address. Now in this case we want the firewall to let all traffic flow to and from a specific IPv6 address without any blocks whatsoever.
First you need to find the IPv6 address of the host and then create a new rule. The new rule would look something like this:
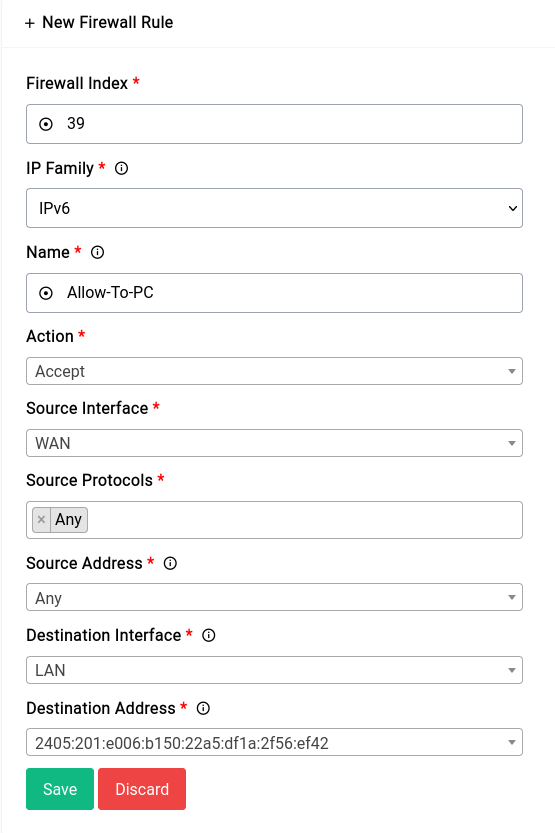
Firewall - Traffic Rules - IPv6 Rule

